Workforce Identity Management Capabilities
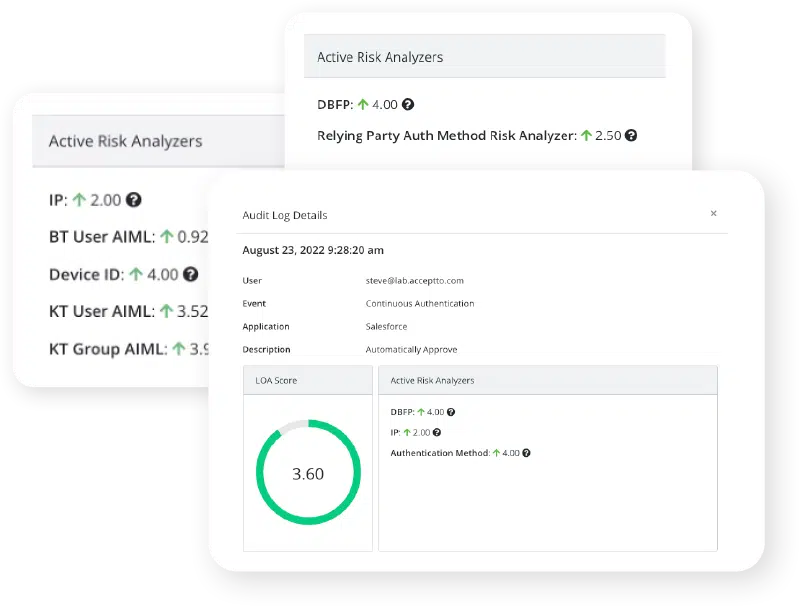
AI / ML Behavioral Risk Modeling
Why AI / ML behavioral risk modeling capabilities matter for better workforce identity management.
For your employee
“I’ve worked in other places where getting access to company resources was cumbersome…but now I feel like I am always asked for just the right amount of information.”
For your company
“We mitigate risk with a more proactive and effective approach that takes advantage of the latest technologies to protect our organizational resources.”
Related Resources
ARTICLE
Identity 101: What Are Geo-Location and Geo-Velocity?
REPORT
Workforce Identity Management Overview
REPORT