Introduction
WHY IS ADAPTIVE AUTHENTICATION AN IMPORTANT SECURITY TOOL FOR FINANCIAL SERVICES ORGANIZATIONS?
The accumulation of data by enterprises and the growing number of cyber-attacks have made adaptive authentication imperative to protect valuable assets. Financial services companies must know and monitor who is accessing what, the time resources are accessed, and how the resources were accessed. These organizations are adopting adaptive authentication to appropriately grant their users (employees, partners, customers) the right access. This report looks to address the challenges of securing users’ identity within financial organizations, and sheds light on potential solutions to these challenges.
Current security challenges within financial services
Unsurprisingly, financial services enterprises are among the most targeted by bad actors or cyber-attacks. As of the most recent data from the Federal Reserve’s 2023 report, there were significant increases in non-cash payments in the U.S. The total number of financial transactions, including debit cards, credit cards, and prepaid cards, reached approximately 262 billion in 2021. The rapid growth of these transactions puts sensitive payment information into the hands of banks and credit card companies. Coupled with the growing world population and the demand for financial products on digital platforms, the vulnerability of digital financial transactions continues to grow, as they are now being exposed to more threats than ever before.
While cyber-attacks affect all industries, financial industries are disproportionally impacted. According to the Identity Theft Resource Center (ITRC), attacks against financial services companies jumped by more than two-thirds (67 percent) year-over-year to be the most compromised industry in H1 2024.
ITRC has observed significant trends in data breaches within the banking sector and other financial services.
Types of Data Breaches by Method:
- Phishing and Ransomware: Phishing remains a leading method, but ransomware attacks have seen a dramatic rise, doubling each year since 2021. Ransomware is expected to overtake phishing as the top method of compromise (Identity Theft Resource Center’s 2021 Annual Data Breach Report Sets New Record for Number of Compromises).
- Credential Stuffing: This method, particularly in Q2 2024, resulted in a significant number of breaches, including a massive breach affecting over 900 million customers of Snowflake cloud services
- Supply Chain Attacks: There has been an increasing number of supply chain attacks targeting financial institutions, contributing to the rise in compromised records (Identity Theft Resource Center Sees Third-Most Data Breach Victims in a Quarter in Q2 2024).
Breach impact on brand and compliance for financial services
Data breaches lead to both brand reputation damage and compliance issues. It’s imperative for financial companies of all sizes – from large global institutions to community banks and credit unions, to protect themselves from bad actors to remain in compliance with local and federal regulations. Under the Know Your Customer (KYC) procedures and Bank Secrecy Act, financial institutions are required to collect and store important information such as Social Security Number (SSN), full names, address, employment status, and previous business and financial activities. The accumulation of so much sensitive and private information by financial companies has led to the enactment of policies to set guidelines on how companies should handle this data. The Right to Financial Privacy Act for instance gives the customer of a financial institution the right to some level of privacy. Banks have the obligation to protect clients’ records. The Gramm-Leach-Bliley Act requires financial institutions to explain how they share and protect customers’ information. Finally, the California Consumer Privacy Act (CCPA) also mandates the protection of customers’ digital information.
The Need for Strong Authentication
In order to protect their brand reputations and remain in compliance with state and federal regulations, many financial institutions have implemented two-factor authentication (2FA) and multi-factor authentication (MFA) to confidently secure access for their workforce and clients. However, simple passwords and 2FA are no longer enough to protect enterprise infrastructure. Passwords are easy to compromise because they are easily predictable; therefore, they do not represent an effective barrier to bad actors. Four out of five people reuse the same password across different accounts creating potential risk for all accounts if the password is compromised. While 2FA is a good step towards better identity and access management, and an improvement over password only authentication, there are still limitations with 2FA. For example, knowledge-based questions and answers can easily be socially engineered, hard tokens can be compromised, popular push notifications have been routinely falsely accepted, and one-time passcodes delivered via SMS/text can be spoofed.
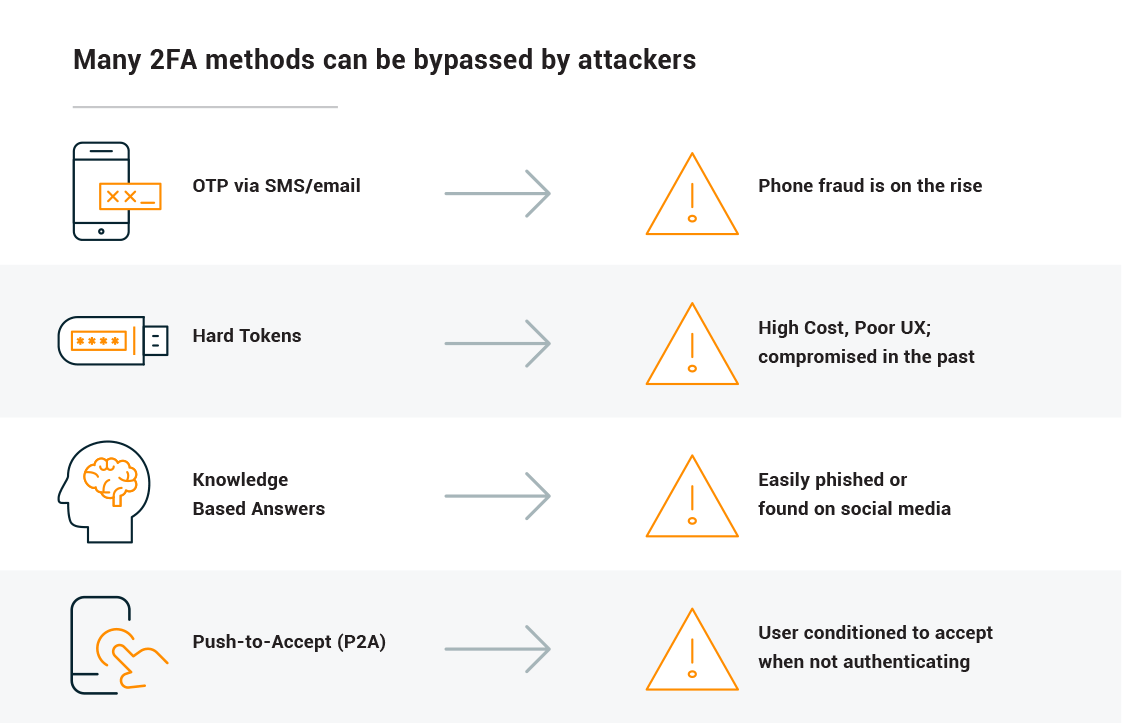
Examples of how two-factor authentication methods can be bypassed by attackers.
While 2FA methods were once secure processes of authentication, today’s financial institutions require more sophisticated solutions to protect against cyber-attacks. To address the shortcomings of 2FA, adaptive authentication has become the new standard. Adaptive authentication adds an additional layer of security to SSO and 2FA based on factual contextual information related to the user requesting access to resources, such as a portal or applications. Adaptive authentication is a method for implementing or selecting the appropriate factors depending on a user’s risk profile and tendencies. These risk-checks occur in the background and are ‘invisible’ to the user, enabling improved security and a good user experience.
“Adaptive authentication adds an additional layer of security to SSO and 2FA based on factual contextual information related to the user.
Adaptive Authentication for Your Workforce & Customers
Many financial institutions are seeking to strengthen end-point security, protect their brand reputation, and meet compliance requirements. Financial services organizations are looking for a solution that can provide a secure and seamless authentication experience to all their users – both their workforce and their customers.
Financial organizations with a flexible and pragmatic approach to identity access management can use the platform to accelerate the adoption of new technologies, increase security, and meet the organization’s digital transformation goals. In addition, these organizations will also reduce operating costs by decreasing the helpdesk burden and simultaneously improve the user experience and their productivity.
Securing Workforce Access
Employees, partners and contractors are all prone to human-error and can be viewed as the weakest link in any security program. Vulnerability to phishing attacks and weak password management are two of the leading methods attackers utilize to prey on these individuals – especially because so much personal data is easily available online. And once inside an organization, bad actors can move laterally, escalating user privileges to gain access to systems and data. Deploying an IAM solution leveraging a layered approach to security ensures valuable corporate resources are available to the appropriate identity at the right time with the least amount of friction. An ability to construct authentication workflows capable of supporting a variety of use cases from simple to uniquely challenging is a foundational requirement to meet both the security requirements and the expectation surrounding the user-experience.
Securing Customer Access
Because customers connect their digital identities to financial organizations through applications, portals and other systems, these organizations must improve interactions and the user-experience, to effectively capture and retain customers. Financial organizations are faced with the need to ensure secure access for all customer identities engaging with their business. While at the same time preventing fraud and delivering an engaging and low-friction customer experience that increases adoption and drives better user engagement to accelerate business. Digital transformation is a top priority for most financial organizations and delivering an exceptional customer experience is critical to the success or failure of these initiatives. By delivering a secure and simple login experience, financial organizations can avoid unnecessary compromise between security and the user-experience while protecting valuable corporate assets and the company brand.
Away with tradition
Traditional access management security architectures were designed for an era that is rapidly evolving and no longer provides the dynamic secure access requirements for today’s digital business. With the introduction of SaaS offerings and other cloud-based services, the complexion of an organization’s corporate resources has changed. And due to this digital evolution, a new approach to identity and access management security is required to meet the business and security requirements for financial organizations and their users.
Identity and Access Management for Financial Services
Identity and Access Management is not a one-size-fits-all proposition. Many financial organizations both large and small struggle with Identity and Access Management as a program of ongoing integration. Key to long-term success for financial services organizations is understanding the strategic value of an IAM solution in the context of business operations. Security leaders with a clear view of how an IAM solution supports the business can appropriately apply resources for measured success and push for continuous improvement.
Over the past decade, Identity and Access Management has transitioned from an IT-centric administration and compliance tool to a critical security component in the modern digital enterprise. Protecting the business and supporting a rapidly expanding definition of users, a modern IAM solution must secure valuable resources, support multiple use cases, be easy to use for both administrators and users, provide intelligence, and manage the authentication of multiple user types – the workforce, contractors, partners, and customers.
Conclusions
Balancing robust security and user experience now more than ever is crucial to on-going business success and competitive advantage for financial services. Ensuring organizations have a unified and pragmatic approach to Identity and Access management is essential to ensuring the security of corporate assets and the protection of the company brand. Disrupting users to achieve secure access is not an option and the cost of a poor experience may result in lost productivity, poor engagement, or lost revenue. Ensuring no unnecessary compromise exists between security and the user experience requires a breadth of options including passwordless authentication to protect resources and deliver the perfect user experience every time.
SecureAuth Adaptive Authentication for Financial Services

- The most multi-factor authentication methods – provide options and choices for users while security professionals meet more use cases and conquer security concerns
- The most adaptive authentication risk checks – protect your organization while preserving experience with behind the scenes risk analysis that will not burden users
- The most federation protocols – deliver a unified and seamless user experience for all your workforce identities
- Infinite authentication workflows – our highly flexible workflows enable the creation of authentication experiences that meet the security and usability needs of every workforce identity
- User self-service options – self-service features for password resets, account unlocks, device enrollment and profile updates mean users stay productive and you reduce helpdesk calls delivering an immediate return on investment
- Deployment freedom – deploy any way you want hybrid, on-prem, or cloud — our platform delivers the flexibility enterprises need
- Simple administration – globally managed configurations and policies combine with an extensive application template library to enable rapid creation and easy management of authentication experiences
- Intelligent Identity Cloud – cloud-based analytics and administration that employs a big-data approach to delivering identity intelligence that informs adaptive authentication to ensure strong security and maximum usability for all your identities.
